Hello,
Since this summer we receive about 2.500.000 request each month a lot are injection and abuse.
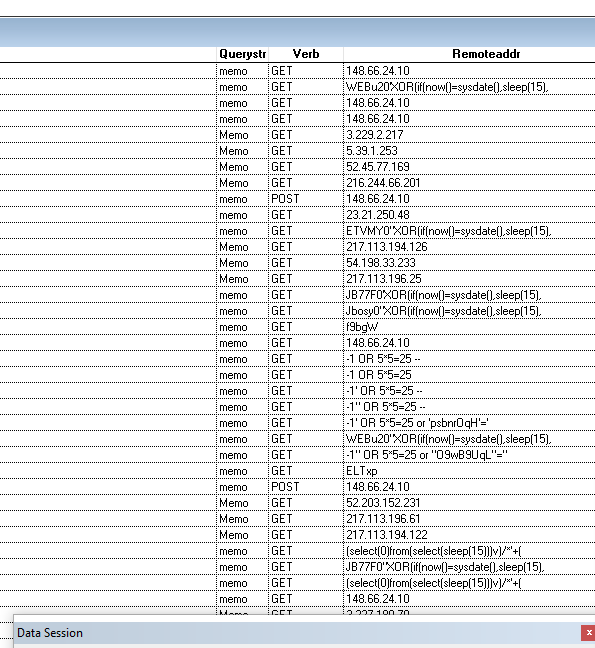
It seems there are tools like ModSecurity for IIS or implementation of reverse proxy, regex rules etc...
Any experience and/or suggestions are welcome
We use Web Connection Handler 8.1.2 (.NET Handler) • .NET 4.6.2 on Windows 2016 Server
Thank you
Marcel

There's not a lot that you can do about that at the application layer.
One thing to consider is running services like Cloudflare in front of your app that basic provide proxying services and they do all sorts of filtering up front. Some of what you're seeing would likely be filtered out before hitting your server in the reverse proxy process.
I'm not familiar with the tools personally, but I know there are dedicated packages of proxies that you can run inhouse to that use white and blacklists to do this without an external service as well, but the problem with those is that they need to be constantly updated.
Big Services like Azure or AWS also have services similar to what Cloudflare does for DNS denial of service prevention but similar scenario: $$$ and you depend on a service.
+++ Rick ---
Thank you Rick,
I just implemented ModSecurity with basic protection like SQL injection showed in previous screen. It's an easy module to install in IIS and it work's perfectly.
There's a active community around this program.
I'm now going to implement the dynamic IP blocking features, there are also Geo localisation tools
Marcel
I was too optimistic with ModSecurity
Without knowing why, I manage to crash the server ( Web Connection and Asp, Html is ok ) from my local computer. Compared to the WAN, the error has not yet occurred.
The error is "The custom error module does not recognize this error."
It seems it could be a ASP.NET error handling conflicts with ModSecurity response processing or a malformed HTTP requests caused by router NAT issues ?
I see you put
Marcel
I could have found the problem, ModSecurity is inspecting the response body and it was during a exe update ( GET /admin/ModuleAdministration.wc ) that the server returns an error ( see it in the ModSecurity log ) or crashes.
The regex engine of ModSecurity could exceeding limits.
Does the exe update go through the server or through the file system. ?
At least the ModSecurity filtering system do is job, the average response time for the server with the most spam was over a second and now it's below 300 ms
Marcel