Hi, we have an EXE that sends out an email that has an embedded link that allows a client to click on the link that generates a URL request to our web app that then has a file sent to them automatically.
We have reports from some clients that they are getting multiple emails when they click on the link.
The code is very simple on the receiving end, we check what document they want and who it is that is requesting it (the URL in the link has that information encrypted) and then create an email, attach the document and send it out.
There is no looping or For/Endfor, While/End While constructs in the code.
A complicating factor is some clients want two emails in their email address (one for the primary person and the second for their secretary/paralegal). So obviously when one person clicks on the link the second person in the email address also gets an email.
Another complicating factor is that one email address may have a rule associated with it that forwards it on to another person or group of people.
It's not all clients reporting this behavior, but those that do claim that only one person is clicking on the link.
Our internal testing has not been able to duplicate the problem.
When I look at the request log for one instance I'm trying to track down, I see the below:
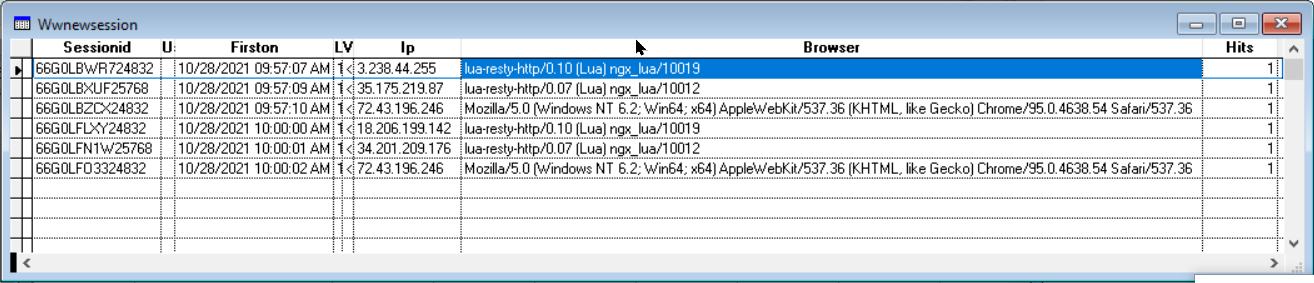 You'll notice that there are six unique SessionIDs, I would imagine that that would mean there were six separate clicks on the link.
However, the FirstOn field indicates that the first three were accepted within seconds of each other, and then the second set was received approximately 3 minutes later, but again the group of three were within seconds of each other.
You'll also note that four of the six IP addresses are unique, with the non-unique IPs related to browsers that match in the first and second group. The third browser has the same IP and description for both groups.
Soooo ... although the client is always right, I'm thinking that my code hasn't even been hit when these entries are made in the Session table (it's named wwNewSession, because it's generated from a query that turned the IP from a memo to a character field), and so they're generated from the client(s) clicking on the link.
We've tried double-clicking the link but we still have been unable to have a single person clicking a link and receiving more than one email.
Is my interpretation of the Session data correct for the SessionID, IP and Browser?
And does anyone know what type of browser a lua-resty is?
My search indicates a Portuguese programming language and not a specific browser, so as you can tell I'm confused.
Any guidance will be appreciated.
You'll notice that there are six unique SessionIDs, I would imagine that that would mean there were six separate clicks on the link.
However, the FirstOn field indicates that the first three were accepted within seconds of each other, and then the second set was received approximately 3 minutes later, but again the group of three were within seconds of each other.
You'll also note that four of the six IP addresses are unique, with the non-unique IPs related to browsers that match in the first and second group. The third browser has the same IP and description for both groups.
Soooo ... although the client is always right, I'm thinking that my code hasn't even been hit when these entries are made in the Session table (it's named wwNewSession, because it's generated from a query that turned the IP from a memo to a character field), and so they're generated from the client(s) clicking on the link.
We've tried double-clicking the link but we still have been unable to have a single person clicking a link and receiving more than one email.
Is my interpretation of the Session data correct for the SessionID, IP and Browser?
And does anyone know what type of browser a lua-resty is?
My search indicates a Portuguese programming language and not a specific browser, so as you can tell I'm confused.
Any guidance will be appreciated.

Bots? Look at the Browser - that's an automated client of some sort not a browser.
+++ Rick ---
Thanks, Rick. I'll check that out with the client. Can you tell me though if each of those entries indicates a hit from the outside either someone clicking in a link that invokes the URL or apparently (possibly) a bot hitting our web server? Again, thanks.
You can't tell how the click is originated. The user agent (Browser in the log) tells you what the client sends, but many bots will masquerade as Chrome or FireFox - a standalone HTTP client can pretty much form up a request any way it wants. So no there's no easy detection of bots that don't want to be detected.
The only way you can detect bots typically is based on behavior. Even IP Addresses often don't stay the same as bot nets run server farms through VPNs.
+++ Rick ---